Data Privacy
Encrypting Data
Vana uses a non-custodial encryption technique to encrypt personal data. The network strives to ensure personal data remains private and is only shared with trusted parties. Data does not leave the user's browser unencrypted. A user's file is symmetrically encrypted with their encryption key, and if the encryption key is shared with another party, the key is encrypted with that party's public key so only the intended recipient can decrypt the key and the data.
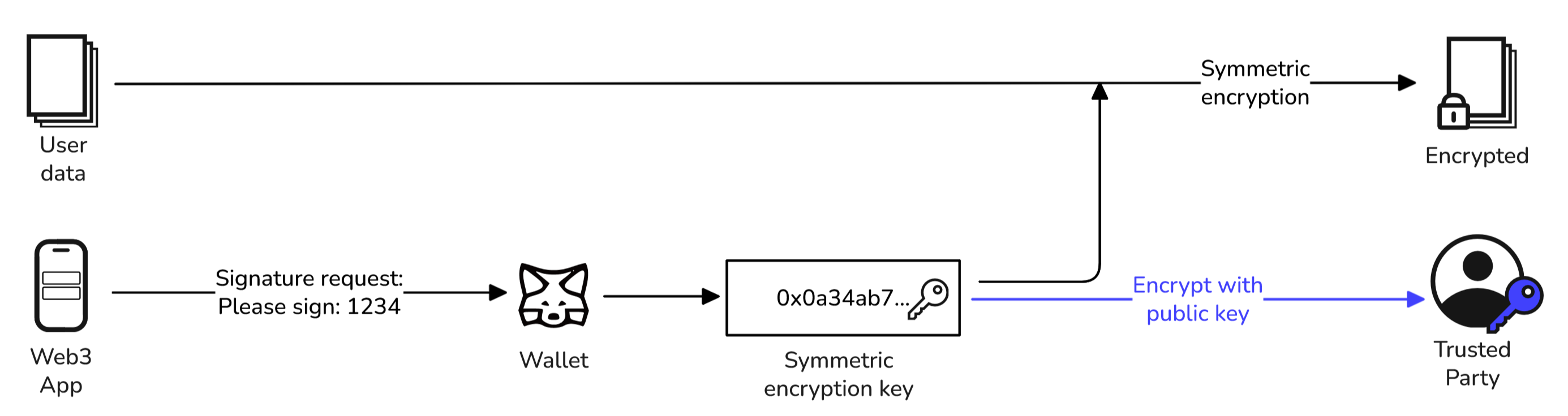
Encrypting user data, and sharing with a trusted party
The steps are as follows:
- The user uploads a decrypted file (F).
- They are prompted to sign a fixed message (the encryption seed) with their wallets, creating a unique signature that can only be recreated by signing that same message using that same wallet.
- The generated signature is used as the encryption key (EK) to encrypt the file F using a symmetric encryption technique, creating an encrypted file EF.
- The encryption key EK is then encrypted with the trusted party's public key, making an encrypted encryption key (EEK). This is known as proxy re-encryption. The EEK is stored on the Data Registry under the file's permissions and can be retrieved by looking up the trusted party's address.
- The encrypted file EF and encrypted encryption key EEK can be safely shared with the intended recipient.
Decrypting Data
Once the data has been encrypted, it can be decrypted by either a dApp or trusted party.
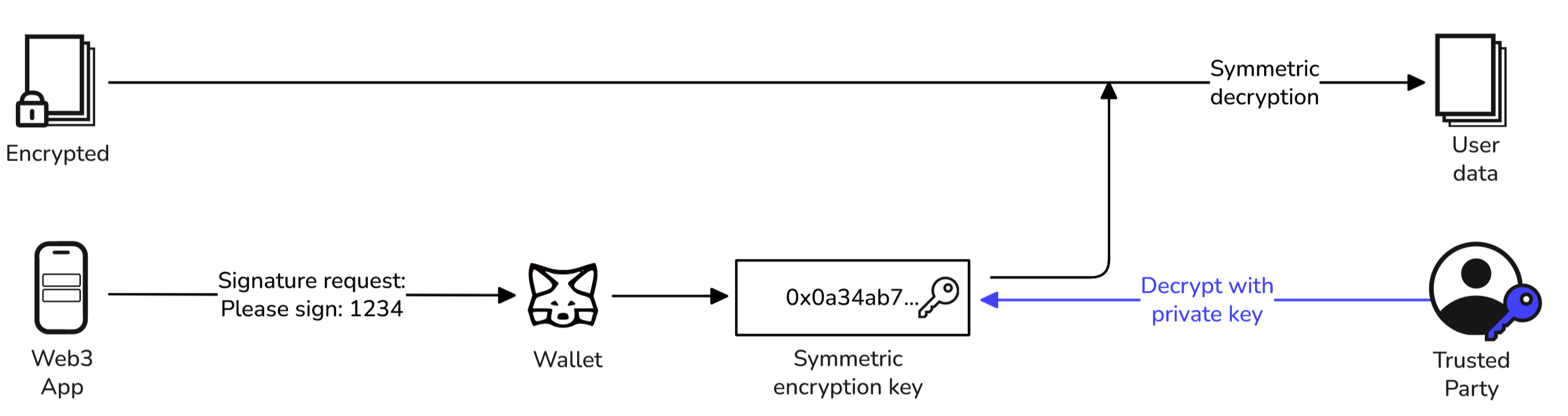
Decryption by dApp
- The dApp prompts the user to sign the same fixed message, to retreive the same EK as above
- The EK is used to decrypt the encrypted file EF and retreive F
Decryption by Trusted Party
- The trusted party receives the encrypted file EF and the encrypted encryption key EEK
- They decrypt the EEK using their private key, to retreive the encryption key EK
- The EK is used to decrypt the encrypted file EF and retreive F
Code Samples
Data DAOs can use the encryption technique described above to efficiently encrypt large files (up to several gigabytes in size) in the browser. Github
If the encryption key EK needs to be shared with a trusted party, it can be encrypted with their public key. To generate a new public/private keypair, see the instructions here.
import \* as openpgp from "openpgp";
const encryptionKey = "0x0a34ab7..."; // This is a secret (EK)
const publicKeyBase64 = "LS0tL..."; // Trusted party's public key, base64 encoded
const publicKey = await openpgp.readKey({
armoredKey: atob(publicKeyBase64),
});
const encryptedEncryptionKey = await openpgp.encrypt({
message: await openpgp.createMessage({ text: encryptionKey }),
encryptionKeys: publicKey,
format: "armored",
});
// encryptedEncryptionKey (EEK) is safe to share with the trusted partyThe trusted party can now receive and decrypt EEK, resulting in EK which can then be used to decrypt the user file F. A Python code example of this is shown here.
Updated 3 months ago
